Blockchain-Secure Identity & Access Management

The theory that all opposing forces find their equilibrium-state either naturally and-or with human assistance holds true for most things: Our planet’s opposing poles – North and South, for Newton’s 3rd law of motion, as it does for ballistics and armor, crime and policing, sadly though, not for e-Security and e-Crime. Which has had a major impact on us all.
Despite billions invested in e-Security in things such as Cyber-Sec, Network-Sec and so on, use of the term “equilibrium” to describe state of balance between e-Security Vs e-Crime couldn’t be further from the truth. The exponential frequency of incidents clearly affirms the opposite – a growing imbalance. Which most can attest to - having been hacked in some way, shape or form.
Out to solve this imbalance, Hyperscalers- a next gen Original Equipment Manufacturer OEM and Shocard – a Silicon Valley based Blockchain expert, started by identifying its top three-causes, being:
- Tech-limitations in identifying both devices and but more importantly individuals driving the devices;
- Aging log-in authentication methods that ultimately rely on user-names and passwords remain unchanged since the ‘60s even though technology and e-Criminals continue to develop; and
- Immature privacy and data laws coupled with service providers’ inability from a know-how perspective, from a technology perspective to comply.
Go to product page for pricing
Blockchain has the potential to solve the causes of the imbalance that are drowning service providers’ ability to prevent and resolve security challenges and scenarios like below from becoming the norm:
- Governments and large enterprises run 30+ different log ins with businesses and people, each having multiple accounts and points of authentication, each vulnerable to exploits;
- The FBI says they “lost” about 5 months of emails in the period of the Mueller investigation;
- Silicon Valley is abuzz about “Meltdown” and “Spectre” – new ways for hackers to attack Intel, AMD, and ARM processors first discovered by Google and publicly disclosed Jan ’18; and
- “Cyber capabilities of Federal agencies are divided, uncoordinated and duplicative- making them insufficient to address cyber threats today…” said the National Infrastructure Advisory Council.
What is Blockchain?
Blockchain, is a technology that refers to a public, or private, decentralized chain of independent secure data blocks that maintain data integrity and user-privacy in providing secure identity verification and access.
Private-Blockchain or Public-Blockchain? Go to product page for pricing
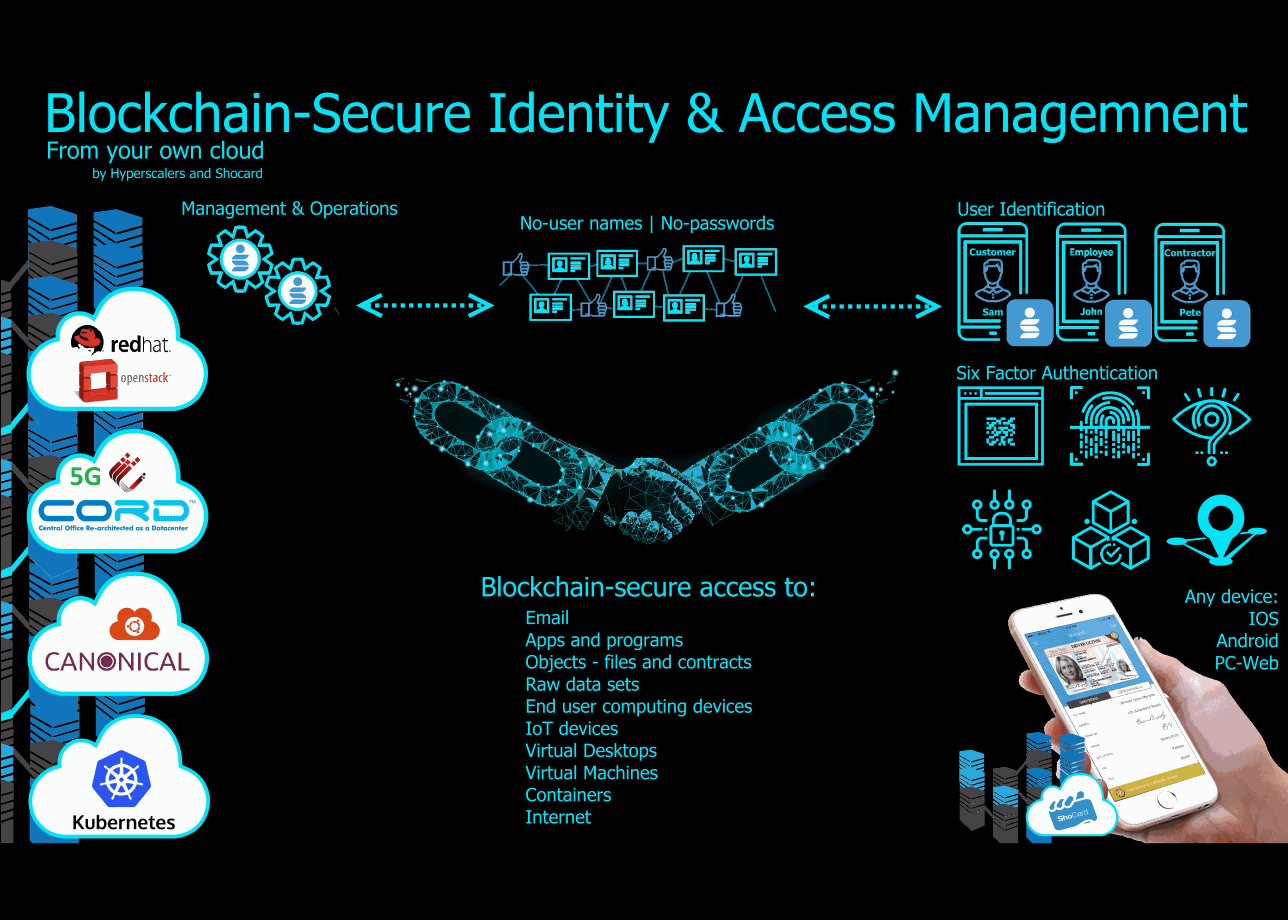
Unlike Cryptocurrencies that use a public decentralized Blockchain, the Blockchain-Secure Identity & Access Management by Hyperscalers and Shocard offers service providers their own private, business-specific, decentralized Blockchain – privately run and operated in their own cloud(s).
The private Blockchain validates its integrity through a decentralized model - running from multiple locations where instances from each location collectively cross-validate each other. In doing so, they eliminate the risk of rogue administrators amending, adding or deleting data without the consent of two, three, four-other appointed administrators.
Service providers can select to run their private Blockchain on either Hyperscale or Tier 1 Original x86 architectures or can select from a productized-appliance such as Red Hat, Microsoft, VM Ware amongst others.
Hyperscale x86
| Tier 1 Original x86
| IP-Appliance Design
| Lab as a Service
|
Who should employ Blockchain-Secure Identity & Access Management?
All medium to very large service providers should take up Blockchain-Secure Identity & Access Management to meet the level of e-Security demanded by both their users and the wider communities in which they operate in; these include:
- Government and commercial enterprises;
- Telco and data providers;
- Infrastructure as a Service IaaS providers;
- Software as a Service SaaS providers and
- Managed Service Providers MSP.
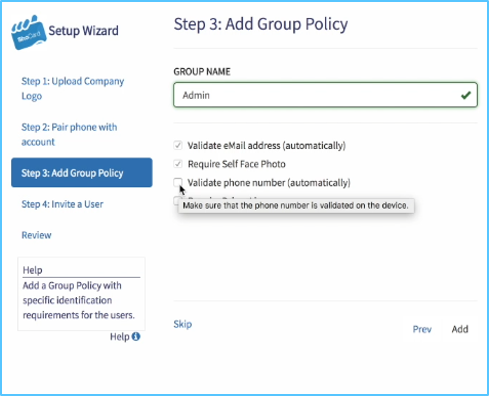
Service providers can meet this demand with the aid of pre-built functions: 
- Geofencing
- Blockchain Validation and;
- Secure Data Exchange.
What do Service Providers need to secure access to?
Simply put, digital services providers need to employ blockchain-secure access to all online services and all wireless or connected electronics, including:
- Email;
- Internet and data;
- Websites, apps and programs;
- Objects such as files and contracts;
- Raw data sets;
- End user computing devices;
- IoT and 5G devices;
- Virtual Machines & Containers; and
- IT infrastructure.
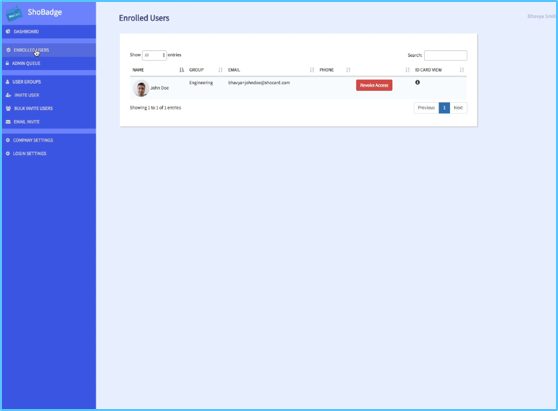
Who are the users?
The users are individuals like you and I and could include: Employees, contractors, customers, stakeholders and clients in general that demand their privacy maintained, their data secured as well as secure access to services offered by providers.
That means no more usernames. No more passwords.
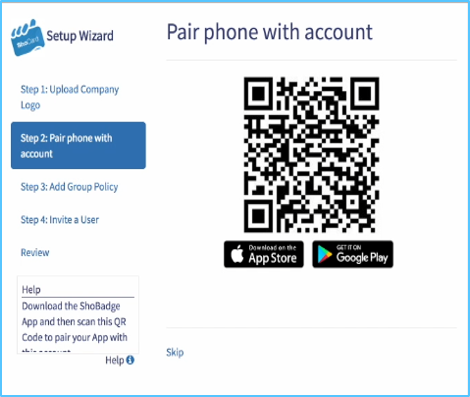
Rather, devices and more importantly the people driving them must be identified through multi-factor authentication methods including:
- Fingerprint scanning;
- Facial recognition;
- Retina scanning; and
- QR-code
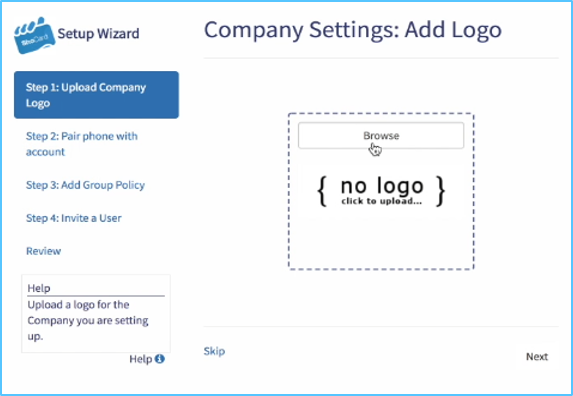
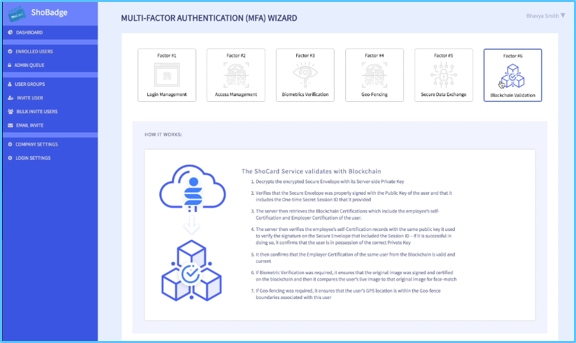
Six 6 Step Configuration Process
We understand that every business is unique. Whilst custom, private Blockchain platforms are available, Digital service providers can their very own using a six-step configuration process.
Step 1
| Step 2
| Step 3
|
Step 4
| Step 5
| Step 6
|
Go to product page for pricing


 AUS site
AUS site