DDoS Mitigation using Cumulus Linux

What is Denial of Service DDoS Attack
A distributed denial-of-service (DDoS) is a large-scale DoS attack where the perpetrator uses more than one unique IP address, often thousands of them.[10] A distributed denial of service attack typically involves more than around 3–5 nodes on different networks; fewer nodes may qualify as a DoS attack but is not a DDoS attack.[11][12] Since the incoming traffic flooding the victim originates from different sources, it may be impossible to stop the attack simply by using ingress filtering. It also makes it difficult to distinguish legitimate user traffic from attack traffic when spread across multiple points of origin. As an alternative or augmentation of a DDoS, attacks may involve forging of IP sender addresses (IP address spoofing) further complicating identifying and defeating the attack.
Visit the Product Pricing Page here.
Download the whitepaper today
Table of Contents
1 DDOS PROTECTION WITH CUMULUS LINUX p5
2 TEST ENVIRONMENT SETUP p6
3 DDOS SIMULATION p8
4.0 MONITORING SYSTEM INSTALLATION p10
4.1 NTOP INSTALLATION p10
4.2 TSHARK INSTALLATION p14
5.0 DDOS MITIGATION p17
5.1 HARDWARE-ENABLED DDOS PROTECTION p17
5.2 INSTALLATION OF DDOS DEFELATE p18
5.3 INSTALLATION OF FAIL2BAN p20
Download the whitepaper today
Images taken from the white paper
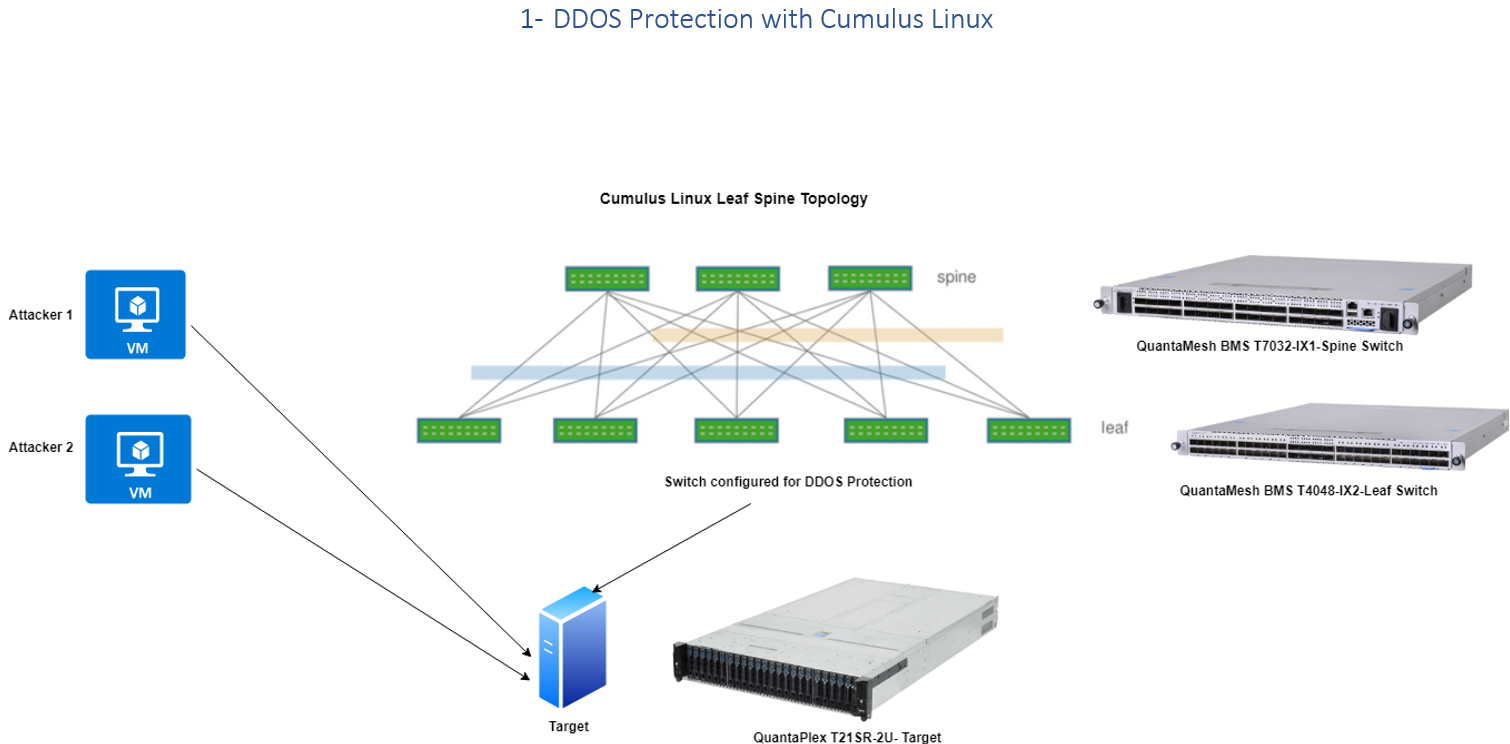 |
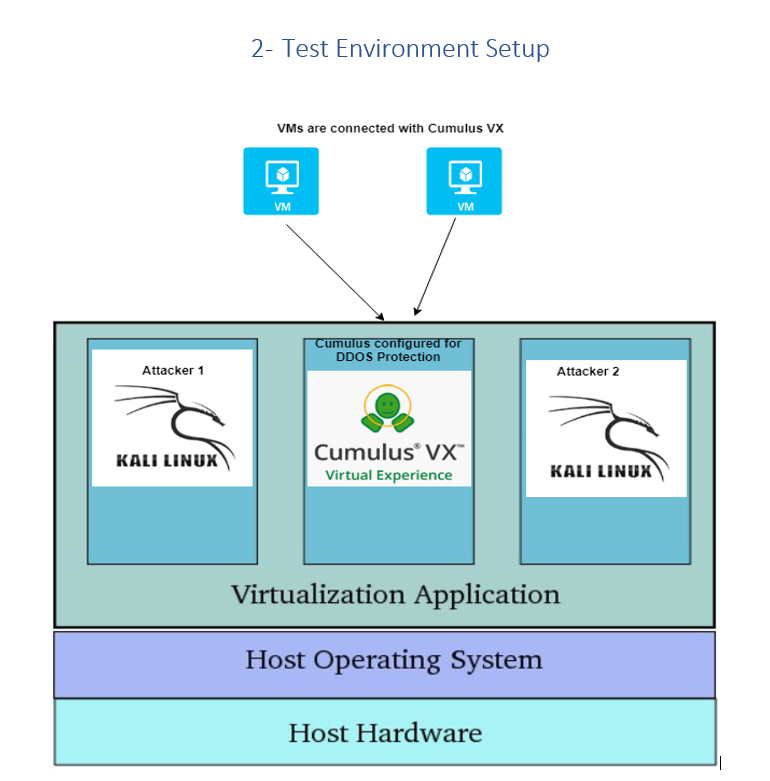 |
100G Secure Tunneling


 AUS site
AUS site