Ridgeback Network Defense
* Ridgeback Business Use-cases:
- Banking and financial services cybersecurity
- The Private Equity Life Cycle Management
- Managed Services and Managed Security Services
- Cyber security for public utilities
- Network Defense in the Manufacturing Sector
- Healthcare and cybersecurity
-
$USD $70.00
*RRP Pricing*To View Channel Discounts Please Login
Hyperscalers with Ridgeback Network Defense
Ridgeback is an active network threat detection, monitoring and response platform. Modern malware, ransomware, and spyware mostly spread through communication platform like emails, where firewalls are not enough to safeguard your network. Traditional, signature-based end-point security solutions are unable to keep up with the daily emergence of more and more malware.
Here is where Ridgeback defence comes into play: a unique, contemporary defence to identify and stop lateral attacks within your network. It is an effective real-time network defence system that runs at the core of your network and safeguards your data.
Ridgeback significantly raises the time and labor cost of attack for the attacker without requiring continual upgrades, giving the company back control.
Ridgeback is plug-and-play, doesn't require extensive configuration or impose any infrastructure burden, starts working immediately after activation, needs little to no supervision, and won't interfere with or burden your live network.
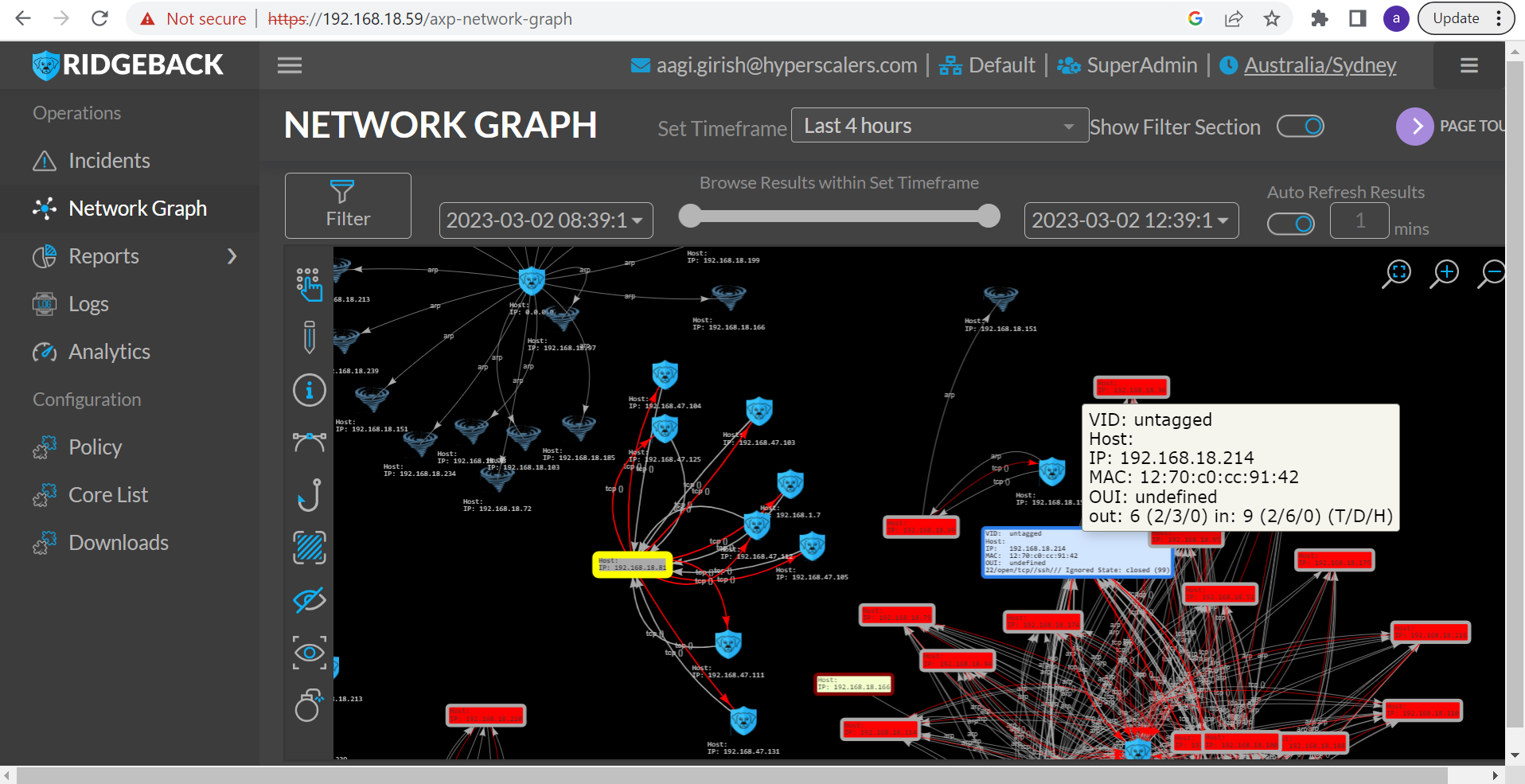
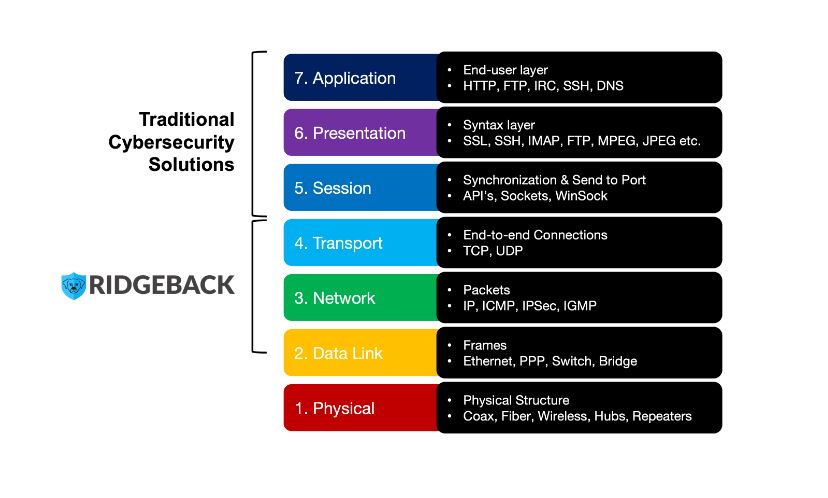
While competing solutions function at higher levels requiring ubiquitous agents, using enormous amounts of resources, and producing several false positives, Ridgeback operates at OSI Layers 2, 3, and 4 and interrupts assaults in real-time by man-in-the-middle automation that engages, disables, and evicts attackers at the start of the exploit.
Infrastructure
Start configuring using Hyperscalers Servers
|
|
|
Download the full reference guide in the downloads tab.
S5K | D43K-1U as a Highly Available two node Proxmox 7.2-11 cluster:
- 2x AMD EPYC 7313 16-Core Processor
- 16x DDR4 3200Mhz 32GB Register Samsung M393A4K40DB3-CWE
- 1x Dual port 10GbE Mellanox Technologies MT27800 Family [ConnectX-5]
- 2x OS SSD WD_Green_M.2_2280 240GB
- 1x Data SSD 2.5'' U.2 NVMe SSD Samsung PM9A3 3.84TB NVMe PCIe MZQL23T8HCLS-00A07
Ridgeback Network Architecture
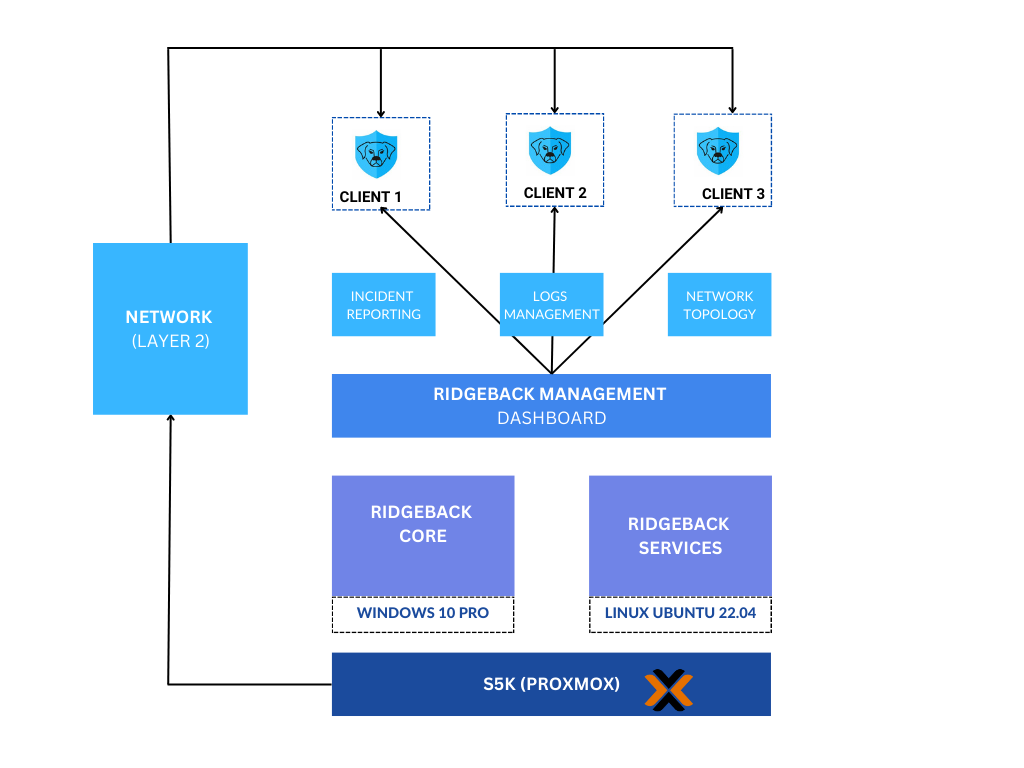
Ridgeback Business Use-cases
Ridgeback can be setup in any network, from small companies to large organizations, due to its strict network Defence features. Due to Ridgeback’s design, any industry like insurance, education as well as government services can use this easy and cost- effective solution to safeguard your network from various threats.
Banking and financial services cybersecurity.
Compliance with regulations necessitates complete, in-depth visibility into system operations. Ridgeback offers insights on weaknesses and productivity issues, particularly when branch office locations are involved across different network segments.
The Private Equity Life Cycle Management.
Catastrophic cyber-attacks on a portfolio can now more than ever decimate a private equity owner's financial return. Ridgeback provides ownership life-cycle services, starting with pre-closing due diligence and ending with a smooth departure.
Managed Services and Managed Security Services.
Ridgeback satisfies situational awareness and security requirements across a wide and diverse client base for an IT services provider thanks to multi-tenancy and an architecture for deployment that is unmatched in its simplicity.
Cyber security for public utilities
As you may have seen in the news, foreign governments as well as ransomware-seeking criminals attack public utilities to interfere with the functioning of our nation. Ridgeback should be utilised to secure the networks of all public utilities since they are all too crucial.
Network Defense in the Manufacturing Sector
OT-heavy workplaces are managed by manufacturers. Ridgeback operates at layer 2, enclosing all networked endpoints within its security perimeter regardless of their hardware, operating systems, or status as managed or unmanaged devices.
Healthcare and cybersecurity
Healthcare and cybersecurity Ridgeback incorporates each networked endpoint, regardless of the kind, inside its security envelope, so you do not have to worry about patient information or the safety of lifesaving IoT healthcare equipment.
Hacker Activity Reporting
Features and benefits of Ridgeback:
Network Protection:
When a hacker tries to get into our systems, Ridgeback defends our systems with the security measures that turns it into a defensive mode immediately for intruders by deploying an automated layers of protection to access any network assets. In simple terms, when an intruder tries to access from a compromised node, Ridgeback can automatically recognize it and raise the alarm on the system dashboard and can isolate the offending node.
Lateral movement Prevention:
Ridgeback enhances security by providing helpful remediation tools that stop security risks' damaging lateral movement. When an attacker gains access to your system, they seek to further enter your network to do more damage. This is known as lateral movement. By limiting the harm done by intruders, the programme rapidly neutralises these security concerns, ensuring the safety and security of your network.
Continuous visibility:
The solution offers total visibility by constantly keeping an eye on your whole network and all the data/information it contains. Your network-connected laptops, mobile devices, and tablets are all regularly scanned for and evaluated for security vulnerabilities by Ridgeback. It makes sure that only people with permission may access your information.
Policy Enforcement:
Ridgeback makes sure that your security policy is strictly followed. Every action on your network is constantly checked against your custom policies, which ensures that all your rules are consistently followed.
Integration:
The programme has useful integrations, such as support for SEIM (security information and event management), so it may be easily included into your current security framework.
User friendly:
Ridgeback's cloud-hosted design allows quick and easy setup. Once it is operating, the system is basically autonomous and doesn't need much supervision.
Start configuring using Hyperscalers Servers
|
|
|
Download the full reference guide in the downloads tab.
Contents Page - Download the Reference Guide in the Downloads Tab
1 Introduction 3
Banking and financial services cybersecurity 4
The Private Equity Life Cycle Management 4
Managed Services and Managed Security Services security 4
Cyber security for public utilities 4
Network Defence in the Manufacturing Sector 4
Healthcare and cybersecurity 4
Network Protection: 6
Lateral movement Prevention: 6
Continuous visibility: 6
Policy Enforcement: 6
Integration: 6
User friendly: 6
Appliance Optimizer Utility AOU 7
Network layer: 10
Containers: 10
Lateral Movement: 10
2 Base Product Deployment 10
3 Configure the Appliance 12
4 Testing the Appliance 16
Policy 18
Creating New Policy 18
Policy Trigger Query Management 21
HS-Policy 22
5 Addendum 23
6 References 27
| Title | Version | Date | Size | |
|---|---|---|---|---|
| Ridgeback Network Defense Introduction |  |
| Title | Version | Date | Size | |
|---|---|---|---|---|
| Ridgeback Network Defense |  |
Tags: Hyperscalers, Ridgeback, Network, Defense, security, threat, detection, data, protection, cost-effective, solution


 AUS site
AUS site